
Get the report
More
Speed up incident investigations by automatically triaging alerts and correlating threats across your on-prem, cloud, multi-cloud & hybrid cloud sources.




Don't let blind spots, expanding attack surfaces and too many alerts drag you down.
Sumo Logic Cloud SIEM provides security analysts with enhanced visibility across the enterprise to thoroughly understand the impact and context of an attack. Streamlined workflows automatically triage alerts to maximize security analyst efficiency and focus.
Coupling built-in event management for team collaboration with an interactive heads-up display, Sumo’s Cloud SIEM enables security analysts to focus their attention on the threats that matter most while they intuitively verify alerts and investigate incidents. Cloud SIEM parses, maps, and creates normalized Records upon ingestion from your structured and unstructured data then correlates detected threats across your on-prem, cloud, multi-cloud, and hybrid cloud environments.
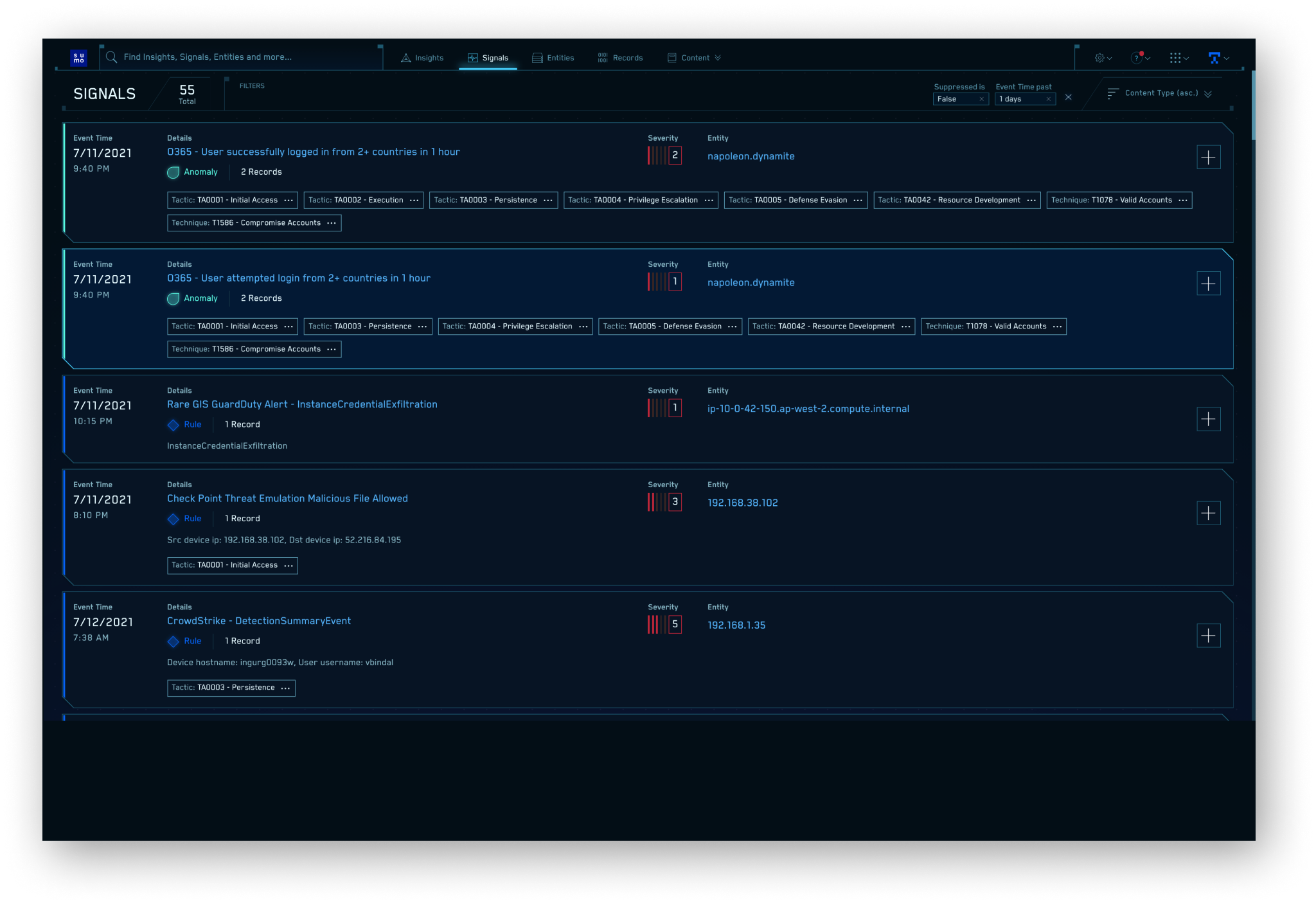
Signals are a collection of alerts, identified through pattern and threat intelligence matching, correlation logic, statistical evaluation, and anomaly detection of your log data. Each Signal is tagged with the tactic and technique related to the MITRE ATT&CK framework using out-of-the-box rules content.
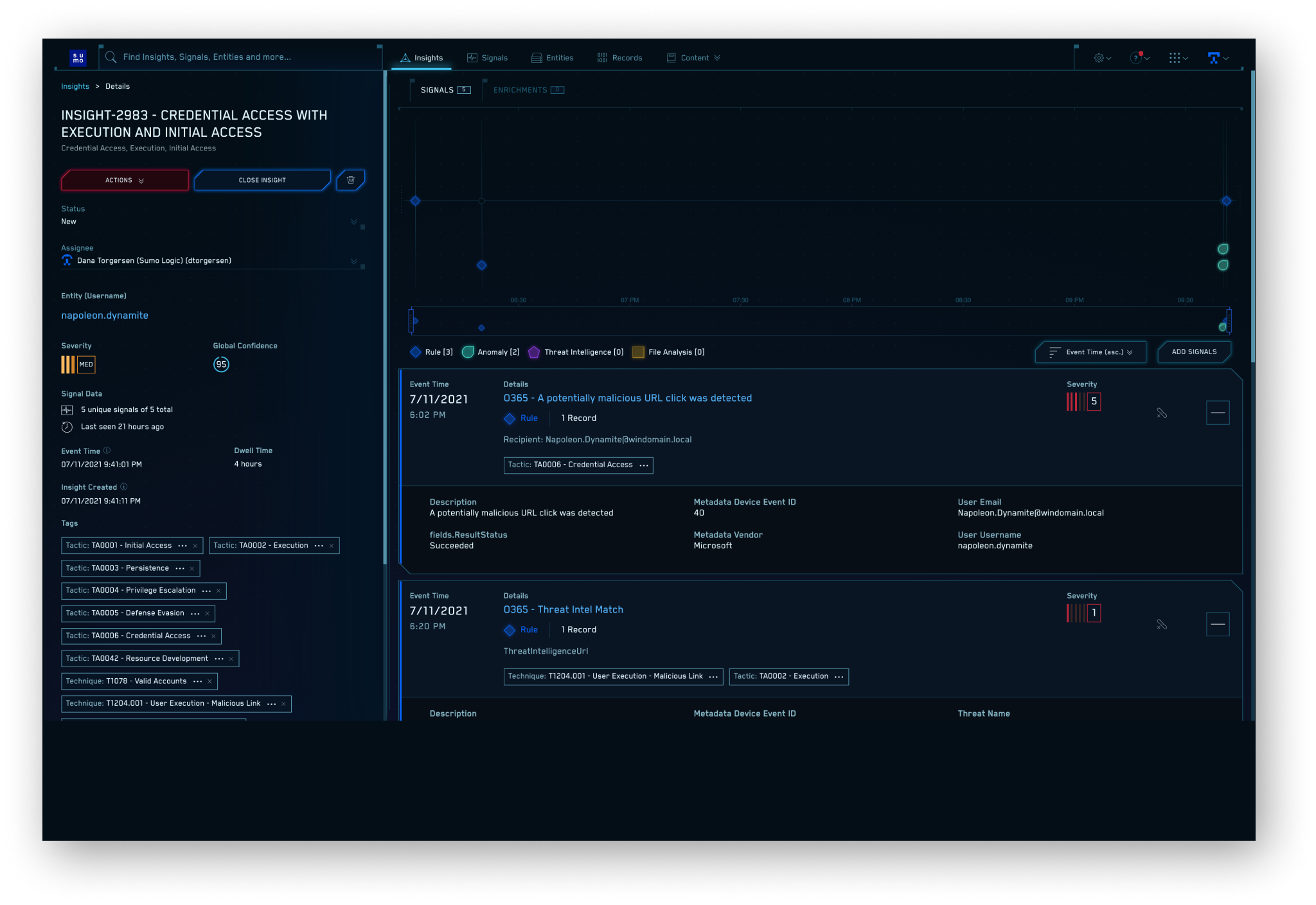
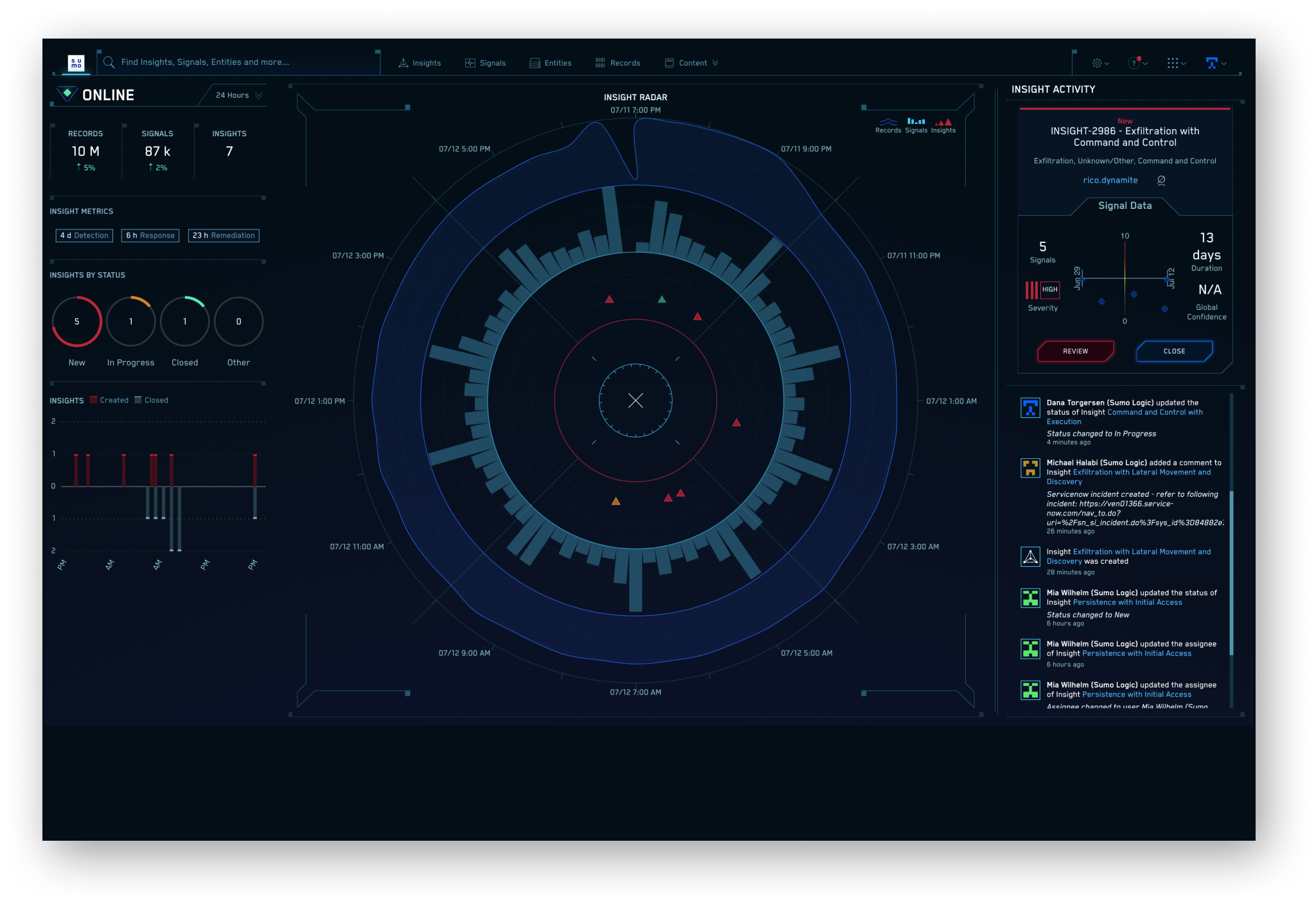
Our Insight engine enables Cloud SIEM to detect advanced threats and low & slow attacks, as well as higher speed direct threats. The Insight engine uses an adaptive Signal clustering algorithm to automatically group related Signals to accelerate alert triage. It also provides a powerful view back in time, evaluating all Signals associated with an Entity for the last 30 days. Once the algorithm determines aggregated risk surpasses a threshold, it automatically generates an Insight.
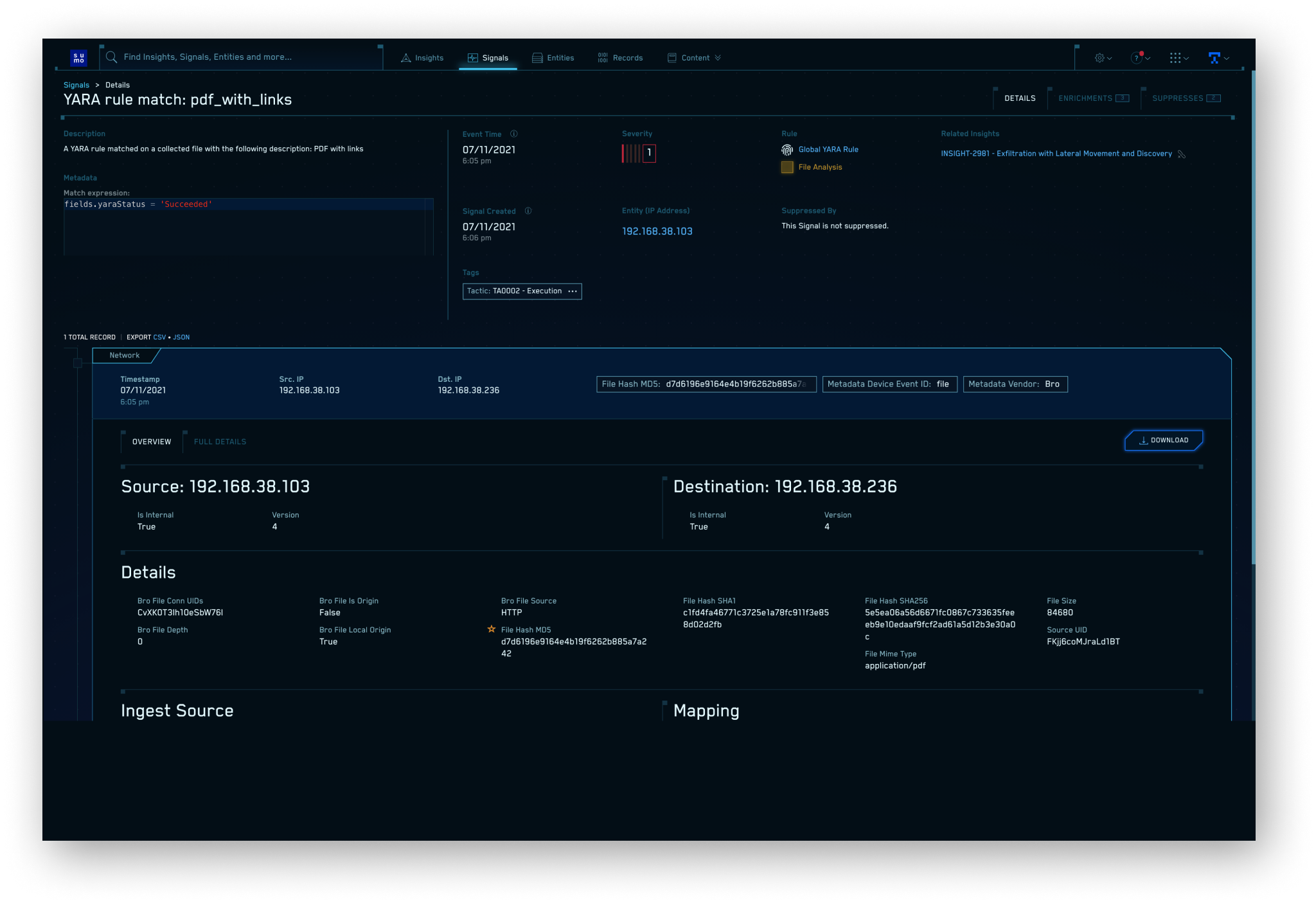
Cloud SIEM ingests and analyzes security telemetry and event logs, but also reassembles network traffic flows into rich protocol-level network sessions, extracted files, and security information. Analysts can see raw network traffic details, related connections and protocol activity, and gain visibility into East/West network traffic. Sumo's deep library of cloud API integrations can pull security telemetry directly from sources such as VMware Carbon Black, Okta, AWS GuardDuty, and Office 365.
Modernizing your SOC—and saving on average four hours per threat investigation while reducing false positives by 90%—requires a completely different approach
Automatically generates actionable Insights (not just prioritized alerts) enriched with user & network context
Multi-tenant scale & elasticity, delivered efficiently at any scale, at any time, for all users
Central security log management for all SecOps, ITOps, & DevOps users—helping consolidate tools
Deep search integrated with highly-tuned, purpose-built security interface with streamlined workflows for security analysts
Cloud-native collection and detection across new threat surfaces from hybrid cloud adoption & digital transformation
Quick deployment with out-of-the-box integrations and content rules in an intuitive platform that’s easy to manage








Experience Sumo Logic’s Cloud SIEM for yourself and see the threats that matter most