
Get the report
MoreNovember 18, 2021
When we talk about emerging technologies and digitization, we often forget that while innovators are working to bring the best solutions to market, cybersecurity gurus are concurrently working to identify loopholes and vulnerabilities in these new systems. Gone are the days when cyber attacks were monthly news; instead, they happen almost daily. With the sophistication of attacks also increasing, CISOs are now accepting the reality that cyber incidents are practically inevitable and planning for a "when it happens" rather than an "if it happens" scenario. As a result, most enterprises have changed their cybersecurity strategies from starting with incident prevention to investing in a security operations center (SOC) to help identify, manage, and contain cyber incidents to reduce the impact on the organization when an attack occurs.
Enterprise SOCs are becoming a crucial part of most organizations’ management departments due to the increase in digitization and interconnectivity. SOCs play a major role in monitoring, managing, and responding to security alerts within a company's daily operations. Since cyber attacks have become more sophisticated, the requirements for SOCs have changed due to increased volumes of data, the complexity of security ecosystem tools, and increased data sources and attack vectors. When it comes to efficiency, SOCs need to expand their focus beyond log management and data analytics to include more advanced functionalities such as automation, leveraging big data and AI for intelligent decision support, and increasing visibility into their product through observability.
Although there is an increasing need for real-time security intelligence through SOCs, most companies are still struggling with inefficiencies. Some are restrained by legacy security information and event management (SIEM) tools that cannot provide meaningful insights or handle cloud services. Most SOCs face different operational and technical challenges that need to be addressed through the use of a comprehensive SIEM that can increase visibility into their daily operations. Sumo Logic’s Cloud SIEM provides security analysts with enhanced visibility across the enterprise so that they can thoroughly understand the impact and context of an attack. With streamlined workflows and automatically triaged alerts, security analysts can maximize their efficiency and focus.
During Sumo Logic’s 2021 Illuminate Conference, Sourabh Bhosale, a Senior Cloud SIEM Engineer at Sumo Logic, shared insights on how Sumo Logic Cloud SIEM is improving daily SOC operations by focusing on the efficiency of dashboards and metrics. We share his discussion of common operational challenges that SOCs face, how Sumo Logic solves these challenges, and which metrics to focus on when evaluating SOCs using Cloud SIEM.
As the technological terrain advances in the areas of cloud migration, digital transformation, IoT technologies, and cybersecurity, most SOCs are facing challenges to keep up with emerging technologies. The increasing complexity of technology has brought about a shortage in SOC teams and prevented them from being able to see the full security posture of their organizational operations. The following are operational challenges SOCs face daily:
Alert fatigue
The “cry wolf” effect (raising the flag before triaging)
The people problem
Tracking KPIs and monitoring SOC efficiency
Alert fatigue occurs when SOC teams become desensitized due to an overwhelming number of alerts, resulting in missed or ignored signals or delayed responses. The fundamental issue with alert fatigue is the overwhelming number of notifications sent within a particular period. Even if a security alarm interrupts a busy SOC team member, it is easier to respond to than a dozen alerts in a row. The higher the number of security alerts, the higher the likelihood of missing something critical. According to findings by Dimensional Research in the 2020 State of SecOps and Automation Report, 83% of IT security professionals experience alert fatigue.
For many SOC analysts, their daily duties consist of reviewing alerts and looking at log data. It can be exhausting to go through the thousands of events that are generated daily. Also, with an ever-changing security landscape, too many point solutions are being developed, which has only compounded the problem. Many solutions out there claim to be preventing the bad things rather than making the day-to-day operations more efficient. Using AI to tackle this problem can sometimes have a detrimental effect because it might cause you to miss legitimate incidents if it’s trained against a bad baseline (meaning an environment that has already been compromised). To sum it up, solving hundreds of security incidents, most of which could be recurring and of low importance, is cumbersome, demotivating, and stressful. Some even call this the biggest cyber threat to watch.
It is not only the multitude of alerts that are challenging for SOCs but also the fact that most of these alerts are false positives. This creates stress and reduces the overall effectiveness and efficiency of SOC analysts. Research conducted by Science of Security revealed that more than 50% of security alerts are false alerts. This is a waste of time for security analysts who spend the majority of their days attending to this high volume of alerts. A report by ESG (Enterprise Security Group) highlighted that 75% of companies spend an equal amount of time (or more) juggling through false positives rather than solving actual alerts.
Analysts should recognize this tendency and rapidly evaluate whether an alarm is true or false. Then, by triaging the alert, they can escalate it to the proper stakeholders. This is what most organizations are struggling with today—differentiating between real and false alerts, then attending to the right ones.
This can be broken down into three categories: staff shortage, skill shortage, and knowledge shortage. Staff shortage is the biggest hurdle in the cybersecurity industry because there just isn’t enough skilled talent. Reportedly, 70% of IT security leaders claim that it is extremely difficult to hire qualified SOC staff. Cloud migration has compounded this issue, as it’s difficult to find candidates with relevant skills.
When employers cannot fill the gaps in their security skill portfolios with new hires, existing staff are left to fill them. If the SOC team does not have the expertise to make full use of their monitoring and security management tools, they will be less effective and slower to respond. This is due to skill shortage.
Knowledge shortage goes hand-in-hand with the skill shortage. Having too little knowledge increases the likelihood that employees will fail to recognize problems. This leads to a failure to respond to real attacks.
The threat landscape is evolving, and effective security programs require actionable information to make informed decisions.
SOC KPIs help improve the security program as a whole and act as drivers for improvement. The challenge here is that there are no set benchmarks for SOC KPIs. These are highly subjective, and meaningful benchmarks can only be determined when organizations know what they are trying to achieve with the program. Additionally, you can’t measure your security if you are not tracking specific cybersecurity KPIs.
Customers leverage Sumo Logic’s security solutions for four primary use cases: audit and compliance, cloud security monitoring and analytics, Cloud SIEM, and Cloud SOAR.
Sumo Logic’s Cloud SIEM provides continuous threat correlation that analyzes several weeks’ worth of data (rather than a few hours’ worth) across your on-premises cloud, multi-cloud, and hybrid cloud data sources using out-of-box content rules. It offers streamlined security analyst workflows that are built by analysts for analysts, along with built-in event management to ensure collaboration and improve efficiencies. In addition, Cloud SIEM provides automated incident prioritization and alert triage, which eliminates the noise and pain of alert fatigue.
Sumo Logic’s Cloud SIEM fits perfectly into Zimmerman Carson's concept of the ”10 strategies of a world-class cybersecurity operations center,” particularly since it acts as a continuous intelligence cloud platform during validation, disposition, and response. Cloud SIEM assists in validating the over 1.1 billion events generated from enterprise operations every day and filters them down to around 10,000 alerts at the disposition level, which comes after validation and typically involves validation of contextual information, tuning of false positives, and forwarding alerts to additional analysts. It then applies basic rules and advanced correlation techniques to bring the alerts down to around 10 (plus) actionable alerts. Although this reduces the number of actionable alerts, you still need to come up with a comprehensive incident report to measure efficiency and monitor the associated KPIs for detections. Cloud SIEM uses the SOC standup application to solve this pain point.
The SOC Daily Standup app, available by request for Sumo customers, is Sumo Logic’s solution for easing the trouble of running a daily SOC operation. We provide a single pane of glass that captures all important correlations and displays trends and alert breakdowns in a given time window. Every entry provides visibility into an organizational-level detection use case. The honeycomb view consolidates the correlations, the alert view, and the corresponding alert breakdown per day. The trend analysis can track all alerts in hourly windows. The information about every alert is color-coded based on alert baselines. Before you decide to build a SOC standup app like this, you need to take a few things into account, including your security infrastructure, the source and nature of your logic, and which features will help your organization meet its particular security goals.
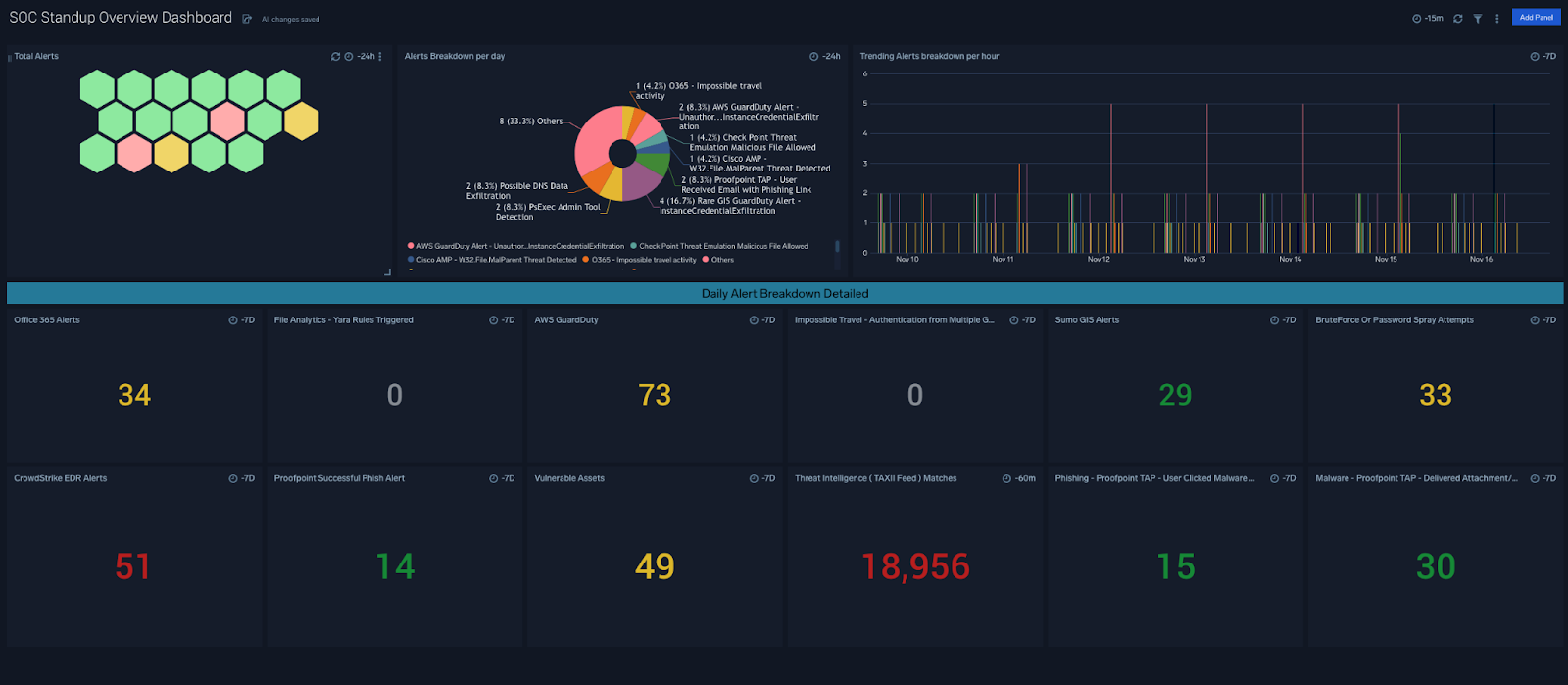
Sumo Logic provides a single pane of glass to ease the trouble of running a daily SOC operation.
Not only does Sumo Logic provide a 40,000-foot view of all correlations, but it also gives a breakdown by alert summary, incident summary, and SOC KPIs. These are all divided into separate panes for easy readability and consumption. All of the dashboards are powered by correlations that are generated by Cloud SIEM, and they also account for the responsible analyst as well as the responses for tracking KPIs.
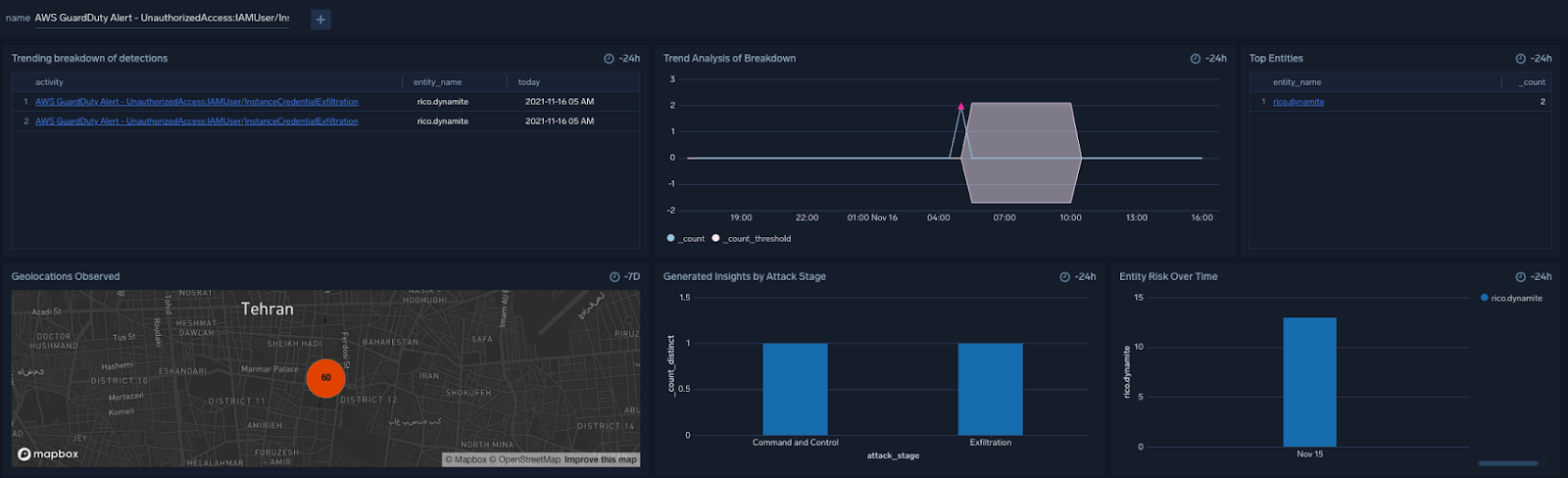
This part of the dashboard is used to monitor alerts that have been fired and provide a summarized version of alerts and behaviors. It displays alert summaries in four parts: alert trends and behaviors, repeat offenders, MITRE ATT&CK mapping, and geolocation information.
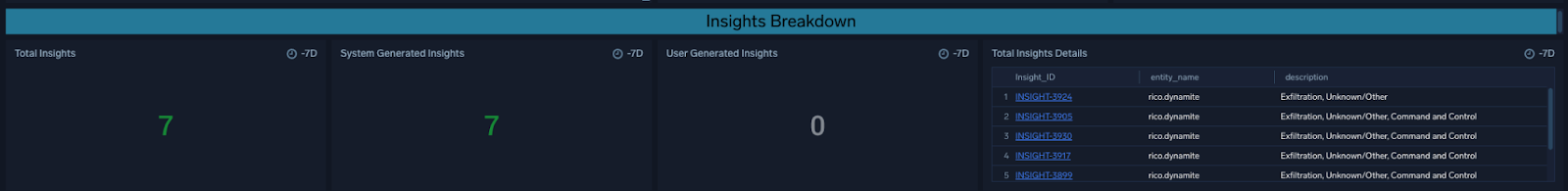
This displays the total Insights of both triaged and prioritized alerts for investigation, including system-generated Insights (which are adapted from Signal clustering algorithms by default), user-generated Insights (which are manually escalated from alerts by an analyst), and Insight details (which consists of a summary of Insights generated in Cloud SIEM).
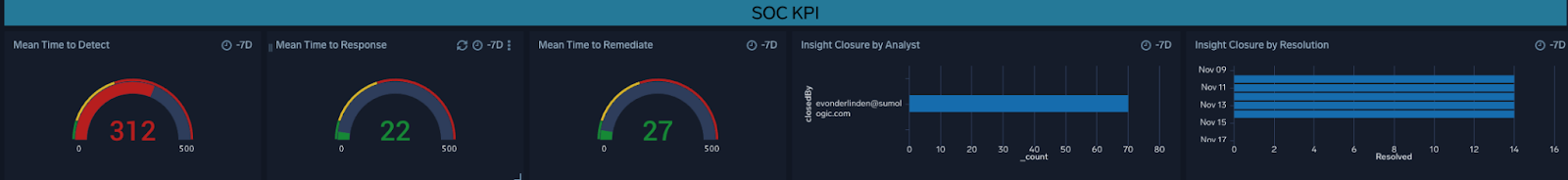
This pane is used to track mean time to detect, mean time to respond, and mean time to remediate Insight closures. It monitors how Insights are being closed by each analyst as well as the type of resolution needed. It also counts the resolution type in a way that makes benign alerts, actual incidents, and false positives visible across the dashboard.
There are three key takeaways to consider in addressing the challenges of tracking SOC KPIs and monitoring SOC efficiencies.
First, you need to know your security infrastructure and identify which detections are important for your organization.
Second, you need to decide which KPIs you are looking to monitor.
Third, you should periodically iterate on the list of alerts you're monitoring and adapt based on the ever-changing security landscape.
Through using Cloud SIEM dashboards in our own daily standups at Sumo Logic we have vastly improved not only our efficiency but our ability to work as a team and understand and emphasize the metrics that matter.
Reduce downtime and move from reactive to proactive monitoring.
Build, run, and secure modern applications and cloud infrastructures.
Start free trial