
Get the report
MoreOctober 19, 2021
Everyone here at Sumo Logic is thrilled to announce our inclusion as a Leader and Outperformer in the 2021 GigaOm Radar Report for Security Orchestration, Automation, and Response (SOAR). We’re excited that our Cloud SOAR solution is getting this recognition and we’re confident that this is just the beginning.
We are even more motivated to keep on innovating and molding Cloud SOAR into a solution that will pave the way for the future of the modern SOC.
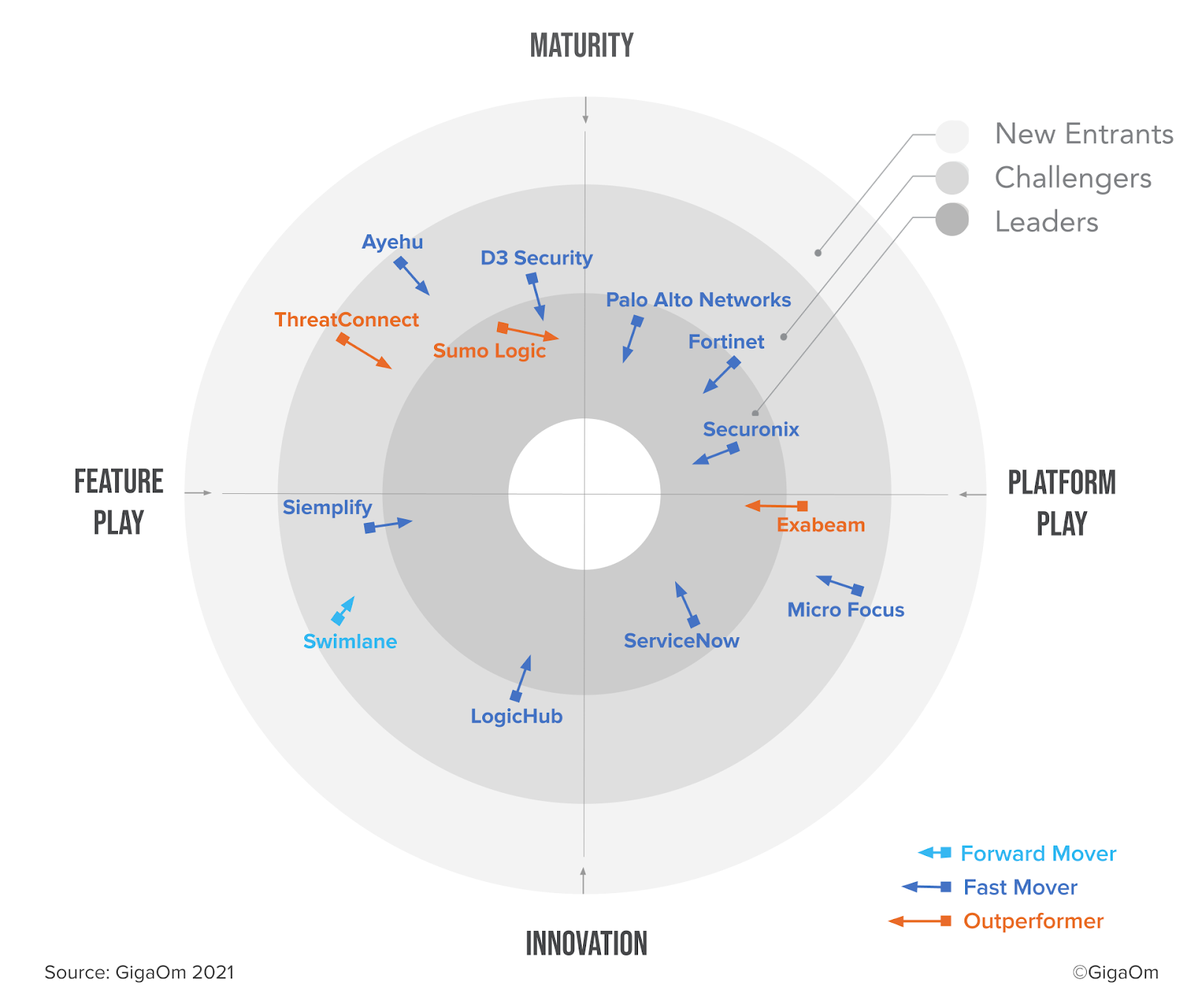
GigaOm Radar for Security Orchestration, Automation and Response (SOAR) 2021
We are honored to be placed as “Leaders” and “Outperformers” in the Maturity and Feature Play quadrant, which we believe is a testament to our dedication to providing best-in-class SOAR technology.
Sumo Logic’s strong ecosystem, fast-paced progression, stability, and cutting-edge functionality have been labeled as the key differentiators that helped establish our Cloud SOAR as a leading SOAR solution in the market.
The report highlights Sumo Logic’s impact in the Maturity and Feature Play quadrant, with a special mention of several key ML-based security intelligence capabilities. Our innovations, Automated Responder Knowledge (ARK) and Supervised Active Intelligence (SAI), as integral elements of our ML security intelligence, have been recognized as key assets in the progression of the SOAR market.
Given that our goal is to empower our customers through Cloud SOAR’s ML-based functionalities, we’re thrilled that our native capabilities have not gone unnoticed.
Secops dashboard configurator
Moreover, GigaOm emphasizes the impact and importance of other Cloud SOAR capabilities, including:
Alert triage
Pre-processing
Autonomous Improvement
Evolving Threat Categorization
Multi-tenancy
Aggregation of events
These functionalities have been labeled as Cloud SOAR’s key assets and play a vital role in augmenting security practitioners in incident management and response processes.
The constantly evolving threat landscape leads to the inevitable SecOps challenges. Cloud SOAR capabilities that are based on machine learning, progressive automation, and real-time analytics help resolve these challenges faster. These capabilities are integral in SAI and ARK, allowing security professionals to make fast, enriched, and data-driven decisions.
By leveraging Cloud SOAR’s machine learning and progressive automation, security professionals can:
Identify false positives from real threats
Improve standard operating procedures (SOPs)
Automate a wide range of low-risk and repetitive tasks
Deduplicate and merge incidents with the same characteristics
Receive playbook suggestions
Furthermore, Cloud SOAR’s progressive automation capabilities allow it to learn the idiosyncrasies of incoming threats, and thanks to its ML-based security intelligence nature, Cloud SOAR uses the knowledge gained from historical data to sharpen its incident response accuracy, yielding greater levels of remediation proficiency.
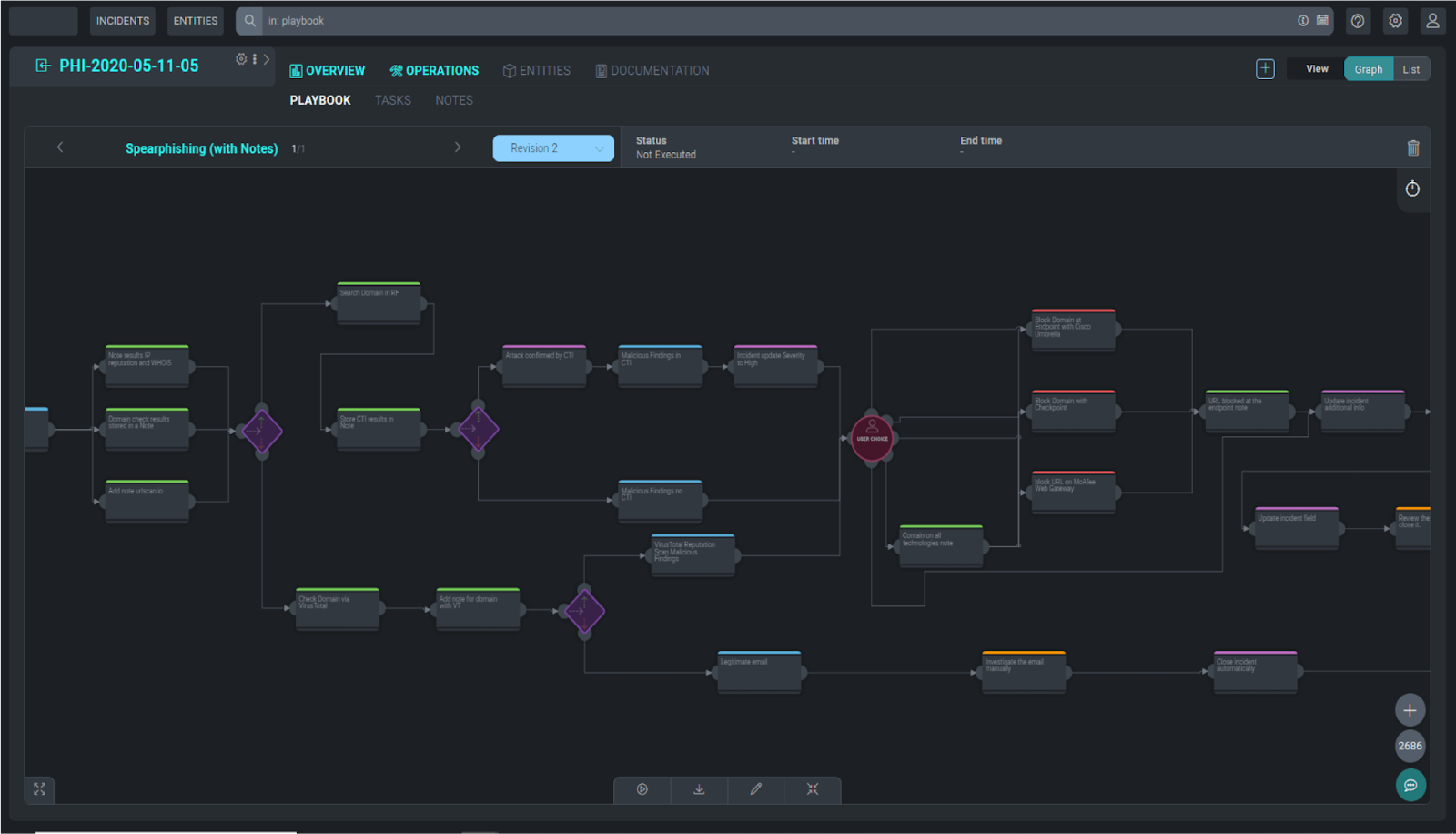
Playbook capability
Cloud SOAR’s ability to apply machine learning to recognize false positives and recommend relevant playbooks allows security practitioners to prioritize real threats and focus on high-priority actions.
Moving forward, we will maintain our cloud-centric strategic approach for the further development of Cloud SOAR. Our goal is to continue to respond to the ever-changing demands posed by the evolving threat landscape by allowing SOC teams to take a proactive stance in alert investigation and incident remediation.
We envision a future where Cloud SOAR is not only a key asset in a SOCs environment but also plays a central role in the heart of every modern SOC. We will continue to develop the open integration nature of Cloud SOAR, as we believe it is one of the building blocks of the next-gen SOC.
Reduce downtime and move from reactive to proactive monitoring.
Build, run, and secure modern applications and cloud infrastructures.
Start free trial