
Get the report
More
Advanced threat intelligence for accurate discovery of emerging attacks, threats and actors.
Patented sensing technology leveraging an invisible polymorphic sensor fabric.
Distributed, invisible polymorphic sensor fabric. Streaming early threat intelligence of attack identification per sectors, technologies and geographic locations. Providing real-time threat feeds into your Sumo Logic platform.
Extend the organization's attack surface with local polymorphic sensors’ replication of real networks. Deceive your adversaries and get a full map of attacks, attack recording, validation of threats and sources.
Understand the rapid pace of real-time cyber threats with our metamorphosing decoys. Continuously collecting and analyzing global threat intelligence from our sensors to deliver the most accurate intelligence about real attacks and future threats.
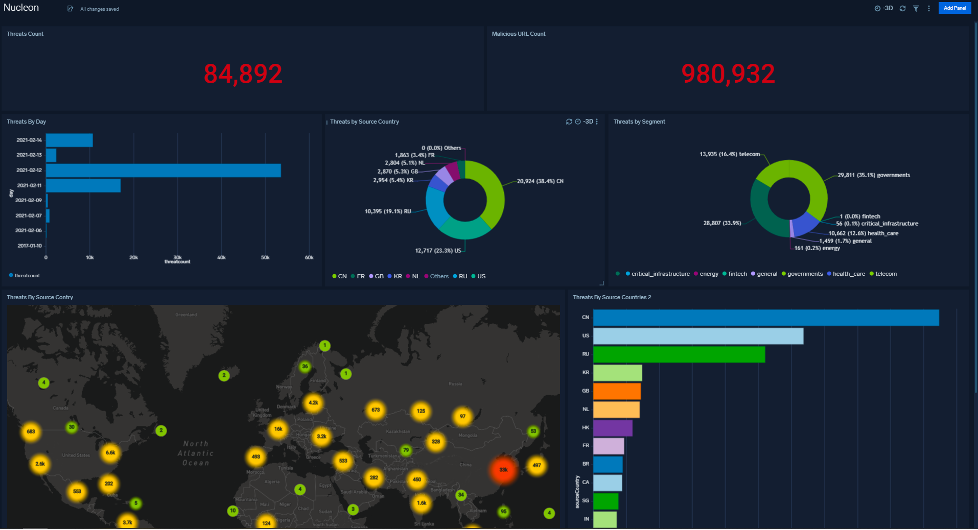
Nucleon offers a new user experience, including actionable indicators and remediation advice that can be implemented in the organization's security operation center (SOC).
We provide only actionable alerts, actively guiding you to block the attack source with the help of your existing defense systems.
From the Nucleon dashboard, you can access threat intelligence assessments, threat alerts, insights and remediation guidance that contribute to a strengthened security posture.
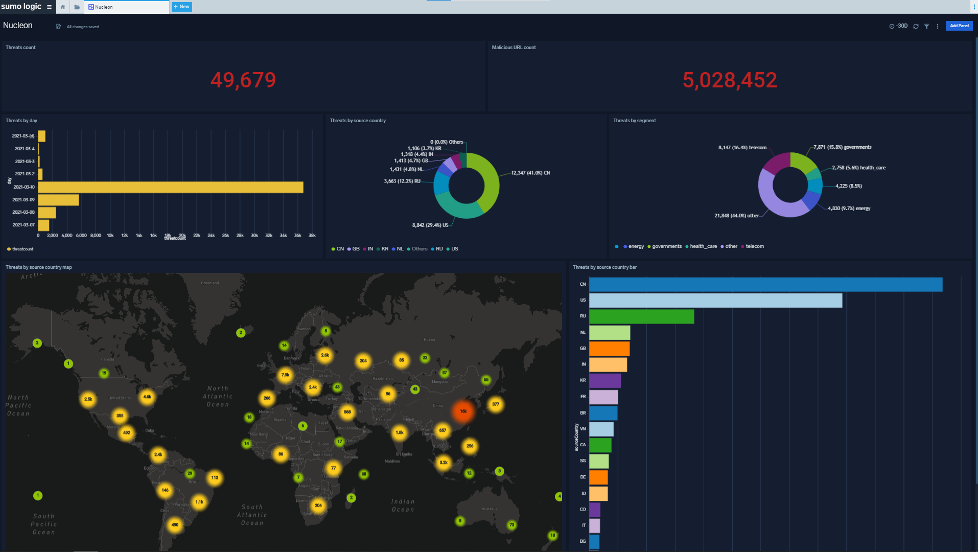
Nucleon models cybersecurity threats so that your organization can anticipate your adversaries’ next move and thwart their attacks.
Gaining visibility into an adversary’s behavioral and infrastructure blueprint is hugely important for the prevention of imminent and future attacks. Nucleon provides analysis of live adversary threat attacks, displaying specific, attributed adversary groups that are targeting your organization, your suppliers, peers, and customers.
Nucleon autonomously processes, verifies and categorizes existing and emerging threats on the different network levels. The system utilizes advanced machine learning technologies and artificial intelligence to perform in-depth analysis, verification, and reporting of threat actors, attacks, and malware. We track and map the potential attack infrastructure – before attacks are ever launched and we evaluate threat severity levels based on patented AI/ML algorithms , adversary intent, TTP and size of attack infrastructure and how it changes.
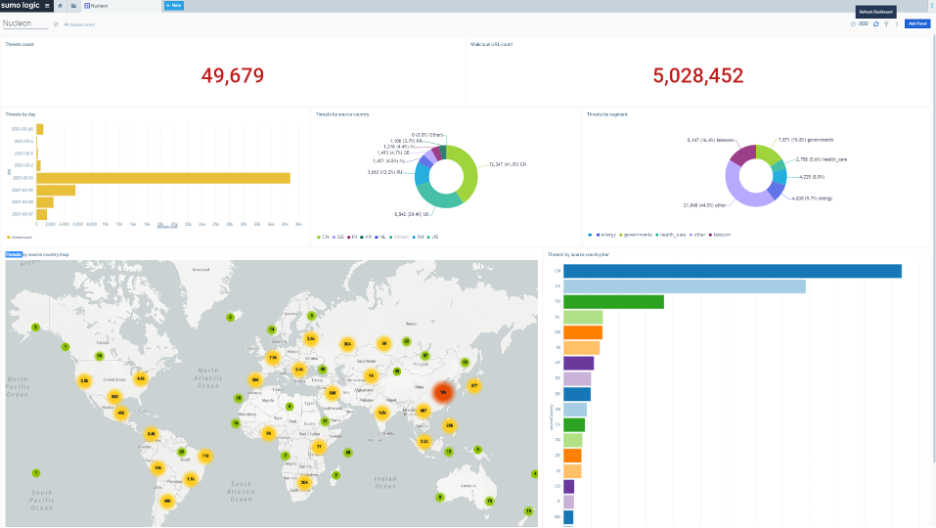
The best defense is a good offense. Nucleon local polymorphic sensors deceive your attackers in order to put them off course, transparently rerouting malicious activity to deception environments. With multiple built-in deceptive mitigations from Nucleon, you can change the economics of an attack to make it more costly, less accurate, and more troublesome for your adversary to attack your organization. Nucleon can strategically and tactically manipulate the attack surface of your cyber footprint, misleading attackers based on your mission and objectives.