
Get the report
MoreProvides the deep visibility needed to stop network-borne attacks early in the kill chain
The ARIA PI application creates unsampled NetFlow or IPFIX metadata for every network packet. This allows for the detection of network-borne attacks, including ransomware, malware, APTs and intrusions early in the kill chain before significant harm occurs.
SOC teams using the ARIA SDS interface, or a SOAR application, can instruct the in-line ARIA SDS instances, to stop the specific threat conversations based on the packet SRC/DST or 5 tuple. All the while leaving critical devices and production VMs online.
ARIA SDS classifies and generates metadata for all network traffic. As threats are detected, via this metadata SOAR applications, can automatically drive the ARIA PI application to redirect data conversations, as set on filters like Packet SRC/DST, for further inspection, by detection tools like an IPS/IPS and DLP.
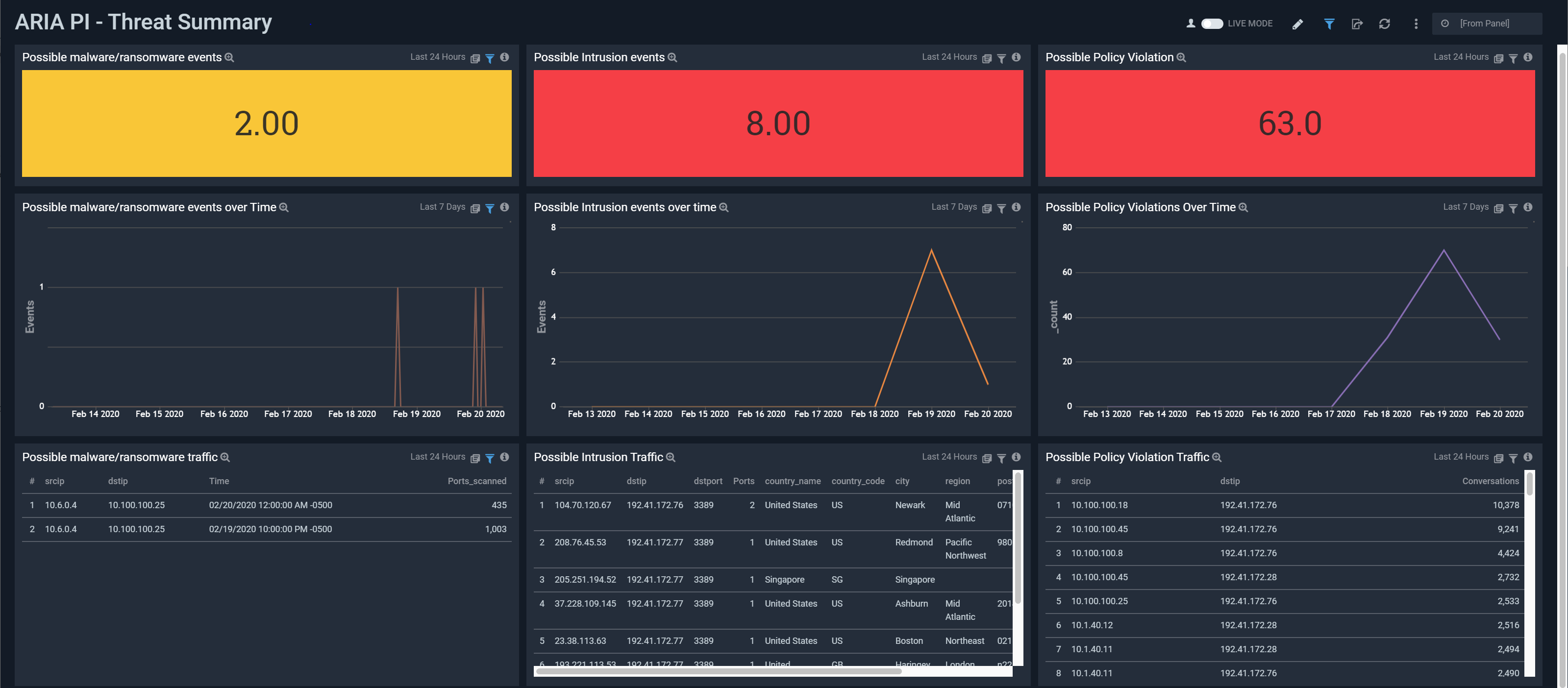
An at-a-glance view, generated by data from ARIA SDS Packet Intelligence, to provide insight into network security posture. This provides a drill down summary of critical threats and attacks
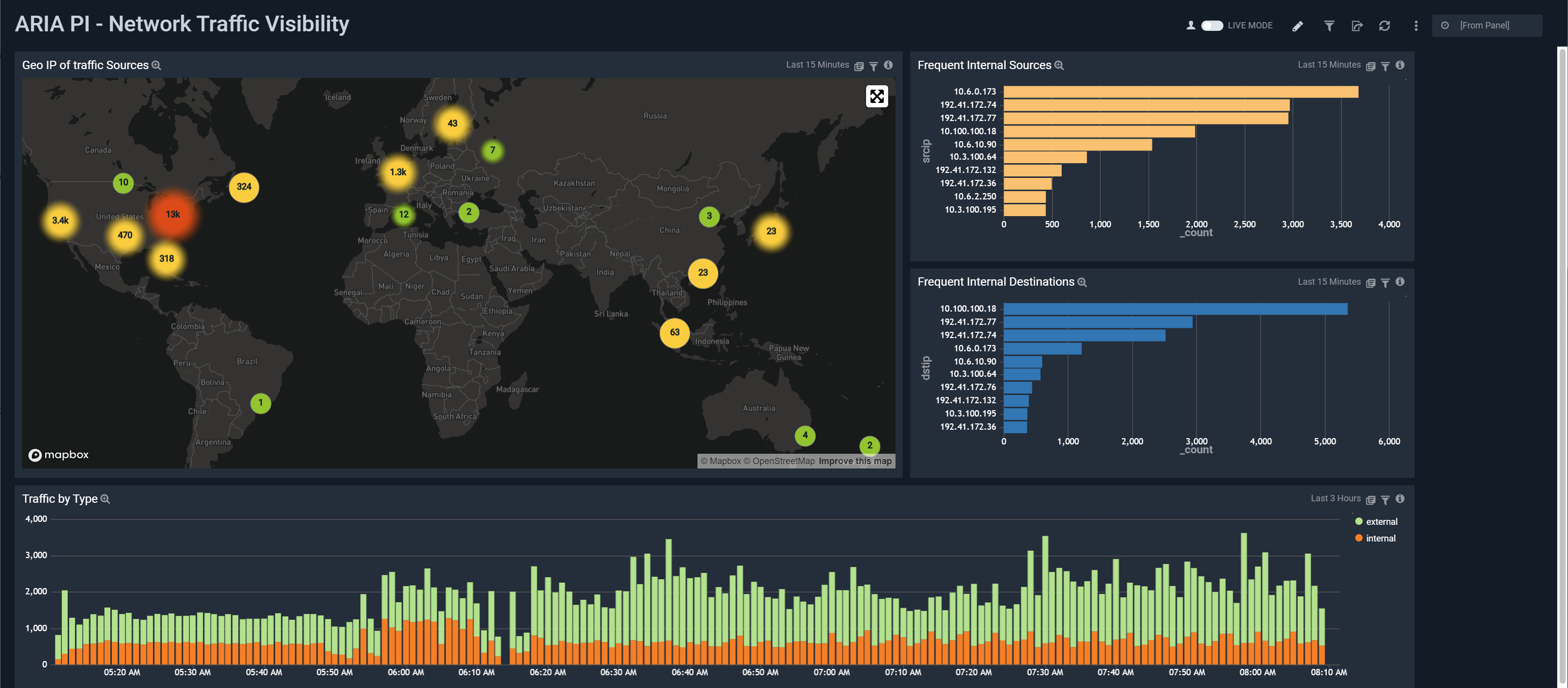
Provides a drill down view as to what is communicating within your organization.