
Get the report
MoreApril 14, 2022

Security professionals involved in the IT and cybersecurity industry for the last 10+ years have most likely come across the terms SIEM and recently SOAR, but there is still much confusion about what the specific use cases and purposes are. So, are these tools the same thing? Do security teams need one, the other, or both within their security operation center (SOC) infrastructure?
Keep reading as we explain their unique capabilities, their differences, and how they can work seamlessly together to accelerate security operations in terms of incident response processes and tasks to help security practitioners wrestle with common SOC challenges.
SIEM stands for security information and event management. This refers to technologies that collect, store, and analyze security data. Examples of data sources a SIEM can aggregate include firewalls, intrusion detection systems, network appliances, servers, databases, and applications—to name a few. Gathering, normalizing, parsing, and storing this data is the information management job for a SIEM.
The SIEM aggregates and correlates all of this ingested data by further identifying and analyzing it. This is often done with the help of special analytics and machine learning software. A SIEM tool checks data for patterns that might indicate an attack and correlates event information between devices for any anomalous activity, issuing an alert if necessary.
Some of the key benefits of SIEM technology include:
Providing SOC teams with enterprise-wide threat visibility
Correlating seemingly disparate security alerts to detect cyber attacks
Thoroughly investigating the activities and actions of attackers or bad actors
Improving decision making and speeding up incident response times
To be able to differentiate between normal and suspicious activities, the SIEM tool needs regular upgrades and tuning. This is often done by security engineers and analysts. Even after a SIEM is properly “tuned,” responding to the alerts generated by the SIEM remains a manual process for security analysts. With most SIEM tools in the market, each alert must be reviewed and investigated by a security analyst to determine if the event is either a false positive or an actual incident that warrants further investigation and remediation.
Also, within today’s threat-prone organizations, there is usually an insufficient number of security analysts available to cope with the ever-growing volume of alerts coming into, and generated by, the SIEM tool. In the case of traditional/legacy SIEMs, a large percentage of these threat alerts are false positives ultimately resulting in wasted time and effort. Meanwhile, it takes just one stealthy, true positive threat to slip through unnoticed and lead to a critical cybersecurity incident. Even when their SIEM tool is successful in detecting threats, security teams frequently find themselves with too many alerts to investigate and their security operations lack consistent, repeatable processes for responding effectively, and quickly, to the threats.
Security orchestration, automation and response (SOAR), terminology adopted by Gartner, is an approach to security operations and incident response used today to improve a SOC team’s efficiency, efficacy, and consistency. To better understand what this means, simply examine its components separately:
Orchestration - the coordination of disparate security tools and technologies used within the tool stack (typically from various vendors) to seamlessly integrate through APIs and communicate with each other to establish repeatable, enforceable, measurable, and effective incident response processes and workflows. People and processes must also be orchestrated properly to ensure maximum efficiency.
Automation - the method of automatically handling tasks and processes, reducing the time these take by automating repeatable processes and applying machine learning to appropriate tasks. Automation helps reduce analyst fatigue or burnout by assigning humans only high-value tasks and decisions.
Response - this describes the approach and steps toward addressing and managing security incidents once an alert has been confirmed including triage, enrichment, containment, remediation and more. Today, many actions, such as quarantining files and disabling access to compromised accounts, can be performed automatically, so incidents that pose a threat can be quickly resolved. Security leaders decide which parts of a standard operating procedure they want to automate and which parts they want their analysts to manually oversee.
In general terms, a SOAR tool starts where the SIEM tool ends—taking over once threat detection has begun. SOAR solutions enable security teams to automatically gather the context needed to further investigate alerts generated from across their ecosystem. By using a SOAR platform, security alerts can be automatically enriched with all the tools and technologies needed, all seamlessly orchestrated together to provide individual pieces of the puzzle. The most appropriate response steps and actions are then executed through the triggering of various playbooks to suit different threats.
This ultimately ensures all security alerts are responded to while freeing up valuable analyst time for them to work on higher-priority, or more complex and proactive tasks, such as threat hunting. When required, they can step into the mostly automated process at any point along the way.
Acting as a force multiplier, SOAR tools allow security teams to do more with fewer resources while providing features to automate, orchestrate, respond and measure the full incident response lifecycle. This includes detection, security incident qualification, triage, escalation, enrichment, containment, remediation and reporting.
Some of the key benefits of SOAR technology include:
Reducing the time from incident discovery to resolution
Minimizing the risk resulting from security incidents
Allowing an easy visualization of response processes
Improving the overall effectiveness and efficiency of SOC operations
Increasing the return on investment for existing security technologies
Security professionals realize the formula for success and improving efficiencies and effectiveness is having both SIEM and SOAR solutions in their SOC. The number of daily security events generated within an organization generally determines its need for a SIEM. The ability to respond to these alerts effectively dictates whether to also implement a SOAR.
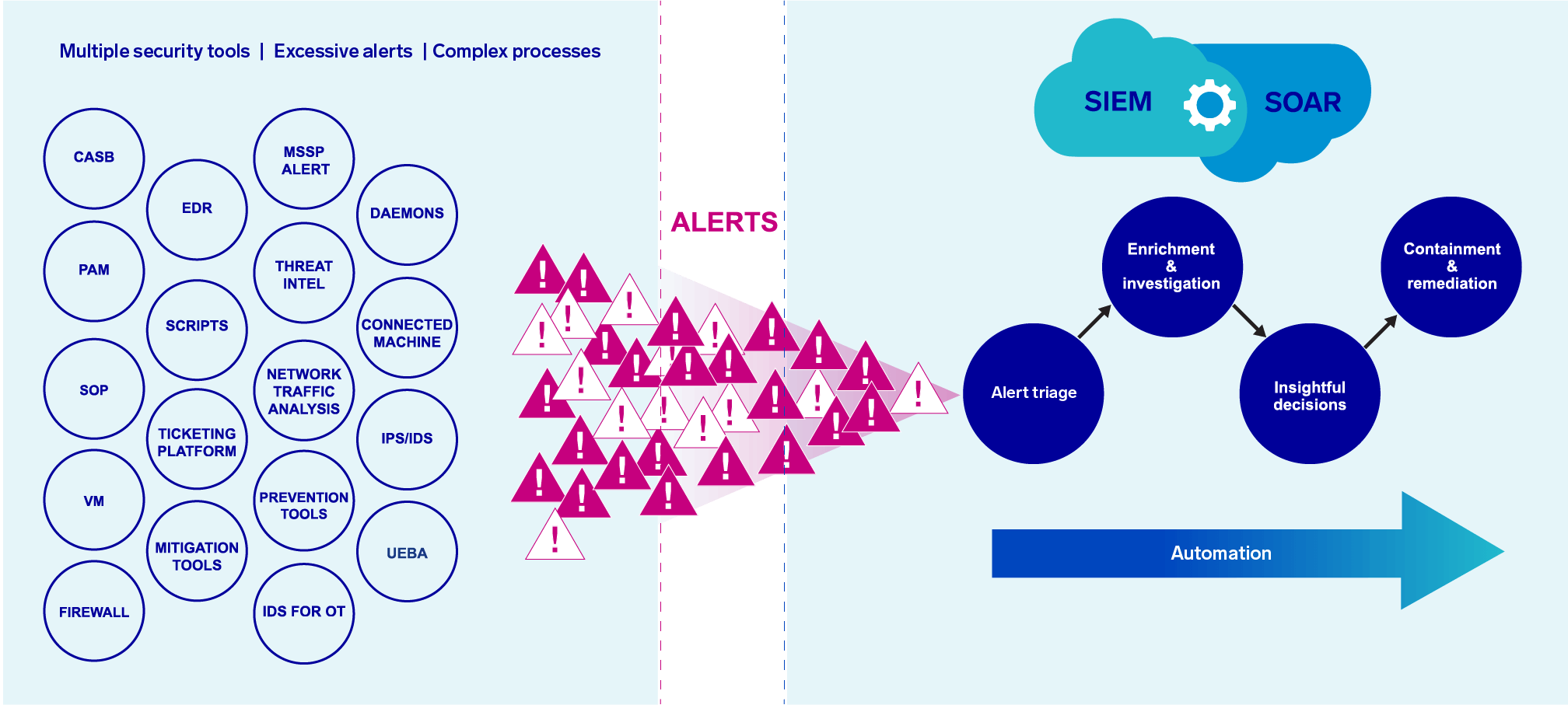
For a large organization potentially receiving hundreds or thousands of alerts per day with a limited workforce, integrating SIEM and SOAR creates a more robust, efficient and responsive security program. Security teams can take advantage of the SIEM to ingest large volumes of data that are normalized into organized records, generate alerts, and prioritize into a triaged view of the true positive threats that matter most to the SOC. Then SOAR can be layered on top to manage the incident response process to each alert, automating and orchestrating the mundane and repetitive tasks which would otherwise take analysts many hours to complete.
SOAR solutions also support full integration with the companion SIEM. Together they ensure no alert goes untouched. More importantly, while working alongside a SIEM, a SOAR solution ensures all alerts are addressed promptly and are acted upon following a standard set of consistent and repeatable procedures. This is critical when it comes to complying with regulations to meet the incident notification and breach reporting requirements while mitigating possible resource constraints or skills gaps.
Here are some examples of how Sumo Logic can improve the efficiency of cybersecurity teams. Working together, Sumo Logic Cloud SIEM and Sumo Logic Cloud SOAR streamline the process of threat detection, investigation, and response.
Actions | Without Sumo Logic | With Sumo Logic |
Alert triage, analysis and investigation | Analysts manage multiple, disparate tools to manually sort through alerts to determine their validity and collect necessary context for investigations. | Sumo Logic Cloud SIEM automatically triages alerts and correlates threats across the SOC team’s on-prem, cloud, multi-cloud & hybrid cloud sources. Analysts are provided with actionable Insights that are enriched with user & network context to eliminate alert noise and reduce false positives. |
Incident assignment | Incidents are assigned through the ticketing system by manually collecting information from different tools. The resulting analysis of the information collected will not be straightforward. | Sumo Logic Cloud SOAR automatically creates incidents only when real threats are detected and assigns them to a specific analyst or group of analysts. Incidents in the Case Manager are enriched with all the essential information, enabling the SOC team to immediately act on them in a collaborative, transparent manner. |
Playbook activation | If the SOC team has written incident response procedures, they have to follow them by managing several tool interfaces. If they lack these pre-determined procedures, then the individuals often improvise based on their own experience and skills. | Sumo Logic Cloud SOAR automatically generates playbook recommendations based on the type of alert. This helps security analysts to activate the correct standard operating procedures and tasks for the specific situation. This also enables the SOC team to scale their response capabilities and improve reaction time. |
Standard operating procedure task management | The SOC team must manage different features across separate tools and follow written instructions (if they exist). | Sumo Logic Cloud SOAR orchestrates the SOC team’s entire security stack and automates time-consuming tasks through progressive automation. This allows users to dictate the exact degree they want to automate their standard response processes. |
Report creation | Analysts have to manually collect all pertinent information and build a report. | Sumo Logic Cloud SOAR automatically creates detailed incident reports for the SOC team. |
Getting Started
To see the power of Sumo Logic’s Cloud SIEM and Cloud SOAR together in action, get a demo and discover how they can help you modernize your SOC! You can also contact your authorized Sumo Logic reseller or contact Sumo Logic directly.
Reduce downtime and move from reactive to proactive monitoring.
Build, run, and secure modern applications and cloud infrastructures.
Start free trial